
In many organizations, security efforts are focused exclusively on deploying technologies, implementing “best practices,” or responding to a continuous stream of alerts and issues. The result is a reactive security organization busy with activity and unable to answer the question, “Are we becoming more secure?” This creates distrust between business leaders and the security organization. Security efforts are seen as expensive—doing more to slow rather than secure the business.

A more strategic approach is necessary—acknowledging the reality that security needs will always exceed security capacity, optimizing security resource allocations, and demonstrating progress toward a more secure organization. This requires the security organization to transition from security operators to security leaders by:

The security organization’s priority is to identify risks, recommend responses to these risks, facilitate the appropriate tradeoff decisions related to these risks, and provide a line of sight to the execution and performance of these risk responses.
A security operating model enables this approach. It governs and oversees security for the entire organization, where the business is not only a recipient of the security services but is also instrumental in the collaboration, implementation, and sustainability of security efforts. The operating model utilizes a risk-based approach to identify and prioritize risk mitigation efforts to secure the enterprise’s mission. The core of a security operating model is a collaborative, continuous improvement process designed to sustain the controls that secure the enterprise.
A comprehensive security operating model includes the following components:
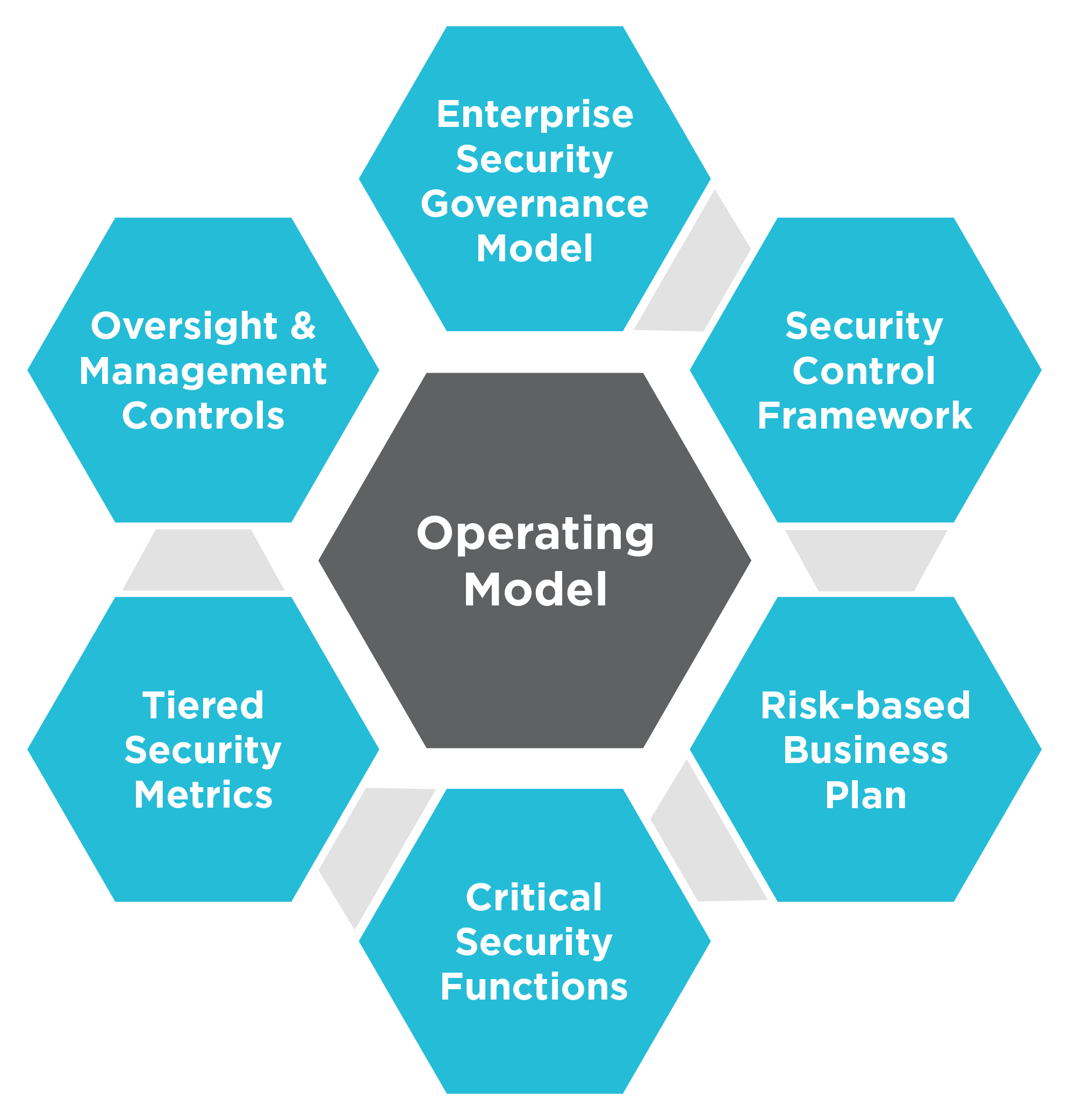
The enterprise security governance model ensures collaboration with the business. An executive committee with a CSO/CISO and senior leadership from across the organization balances the organization’s security risks with the overall costs. Through the operating model, the security leadership provides a clear vision of desired security capabilities and corresponding people, process, and technology enablers.
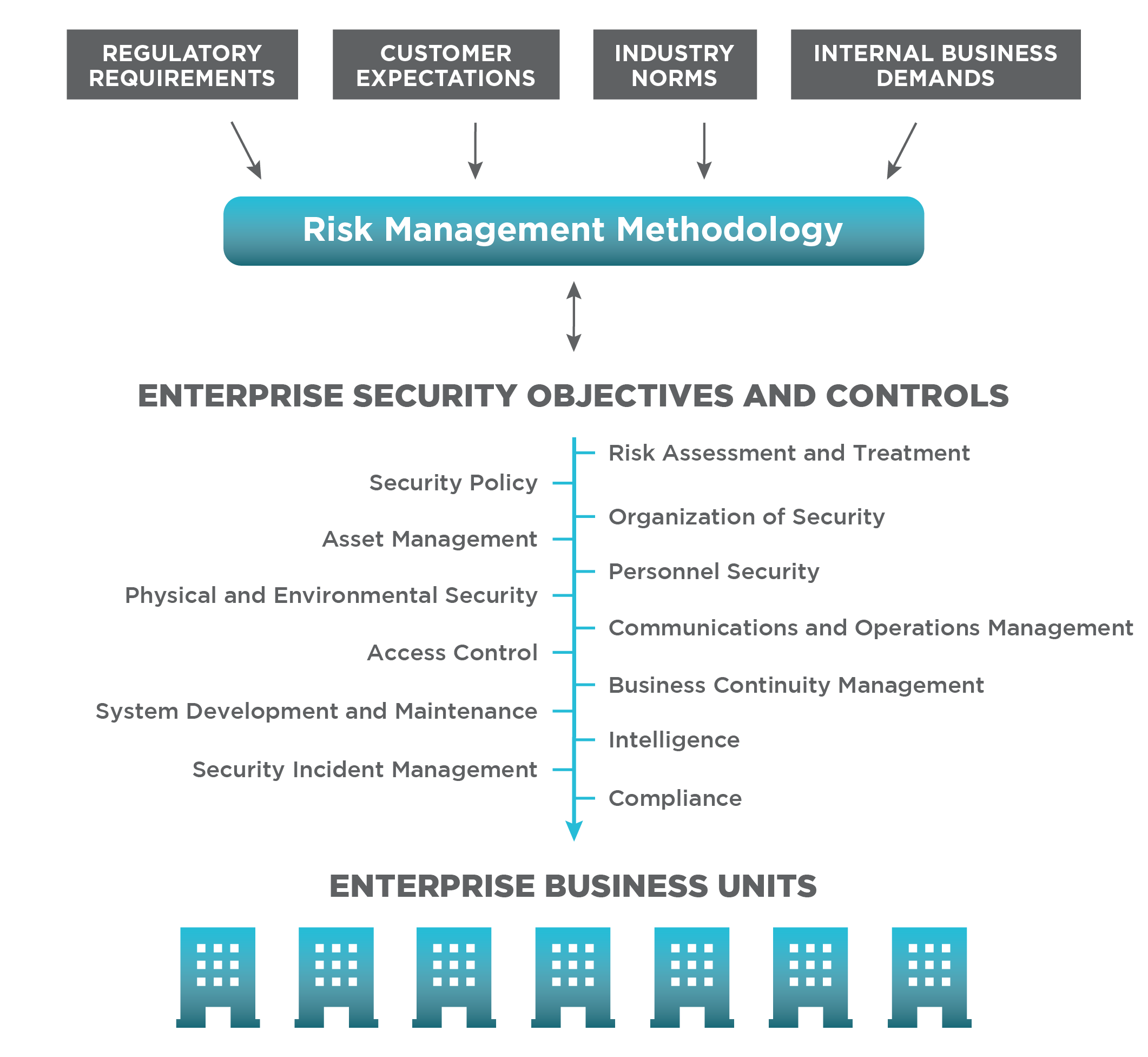
A security policy based on an industry-accepted controls framework provides the structure and guidance to apply best practices and target gaps in potential security coverage. This ensures the enterprise is thinking holistically about its security performance. The controls framework cascades throughout the enterprise to ensure alignment across assets and operating areas. Alignment and collaboration are the keys to providing continuous and efficient operations.
Utilizing an industry-accepted framework ensures alignment with industry expectations and provides a method for regular capability assessment to track and measure progress.
The business plan’s objective is to allocate security resources appropriately based on the risks to the organization. The plan provides a bridge from a security strategy to a portfolio of cybersecurity and physical security projects and programs. The risk-based business plan operationalizes your security strategy by translating enterprise security strategies and concepts into a set of practical plans and actions. The successful business plan aligns with the overall corporate business model and integrates with stakeholder plans and objectives. The four critical building blocks of the business plan include:
Security risk assessment and treatment plan: allows an organization to understand the residual security risk the organization is accepting based on the implementation of a security controls framework, core function performance, and control compliance metrics
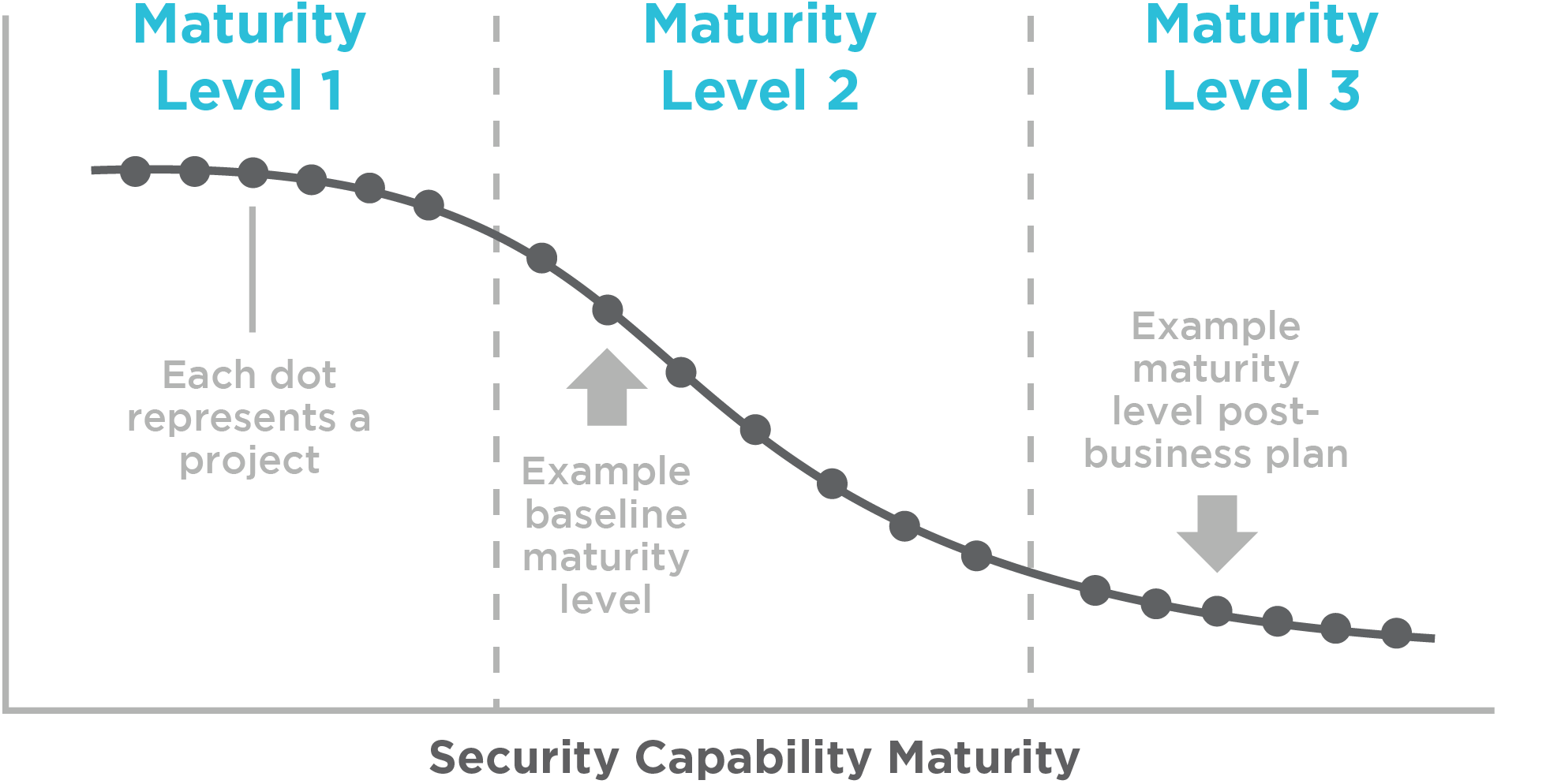
Capability maturity: utilizes a consistent and industry-based maturity model assessment to help identify the maturity level of cybersecurity and physical security capabilities and define target achievement levels. You can also benchmark your capabilities with similar organizations with the results of these assessments
Performance gaps: utilizes performance metrics to provide the security organization and their stakeholders with a good understanding of their control performance and desired targets to support individual strategic objectives
Scope control: uses the respective risk to the organization to determine required changes. Security may look to improve functionality or efficiency of cyber security or physical security controls based on risk. Additionally, the scope of the controls could evolve to apply to a larger subset of assets like infrastructure control systems or the cloud
The business plan is the most powerful tool to ensure alignment across the entire operating model based on risk to the organization.
The desired end state is a security program that aligns with the industry-accepted controls framework and your chosen level of maturity.
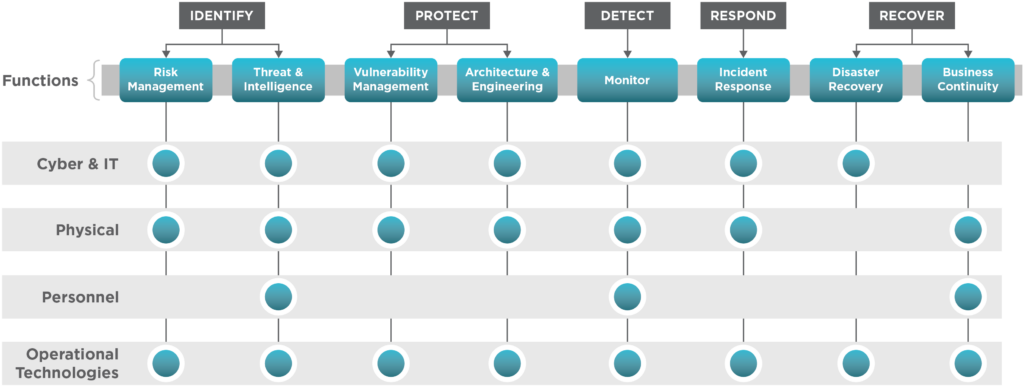
Critical security functions establish clear ownership and accountability and codify decisions on how the organization will run its business. Management uses them to drive performance, continuous improvement, and innovation. Core functions are where the rubber meets the road. When properly established, security functions have the power to:
Functional management provides the accountability model necessary to drive security performance.
“What gets measured gets improved”—security metrics are critical to understanding the health of the function and provide a transparent picture of the security organization. A comprehensive security metrics program serves to unite the operating model with clearly defined goals and measurements to provide a line of sight to performance and enterprise security risk reduction. The key to evaluating the performance is measuring something impactful, then continuously challenging and improving upon it.
Security metrics are critical to understanding the health of the core function and provide a transparent picture of the organization’s security.
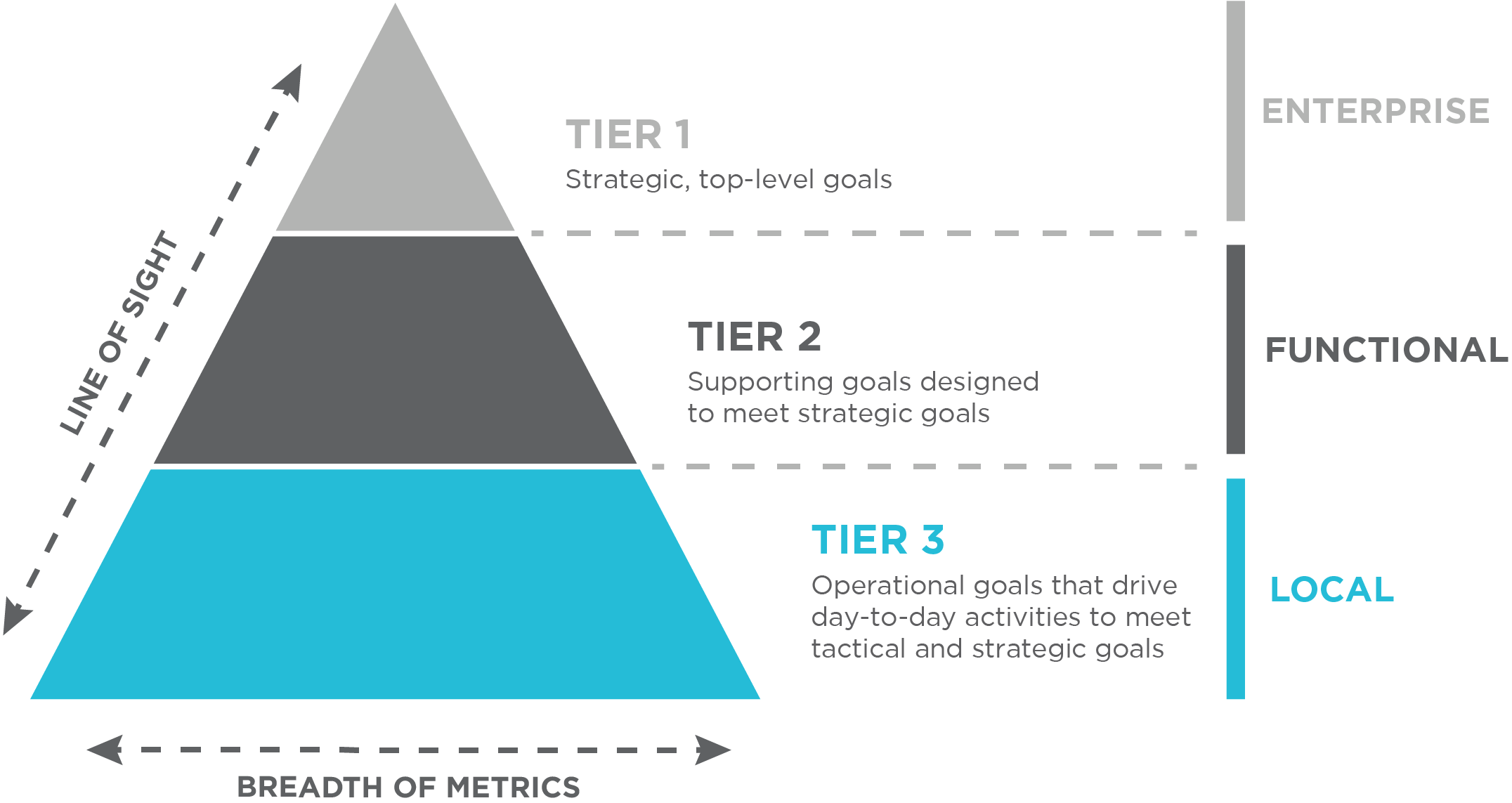
A tiered security metrics program starts with strategic goals that are developed from the top down, including supporting and operational goals. For example:
To learn more about security metrics, read our article: Outcome-Based Security Metrics: An Approach to Improving and Managing Security Performance.
A tiered security metrics program is designed from the top down and developed to support the strategic security goals and objectives. Broader operational performance metrics serve as the foundational day-to-day tactical metrics that can be aggregated at the functional and strategic levels to support enterprise security risk reduction goals.
Oversight and management controls ensure performance meets expectations. Management oversight ensures everything ties together within a continuous improvement loop. The results provide transparency on the adoption of the controls framework, inform the governance structure, challenge the scope, and lead to gap-based and risk-informed initiatives for inclusion in the business plan.
Management controls ensure the organization is readily able to check performance and adjust direction as needed.
Performance Metrics/Goals – Developing, implementing, and monitoring a comprehensive set of core function performance metrics will set expectations and identify gaps or adverse trends
Self-Assessments – Self-assessments answer the question, “How are we doing?” Self-assessments evaluate core function performance in each area by determining current performance, identifying gaps between current and desired performance, and defining strengths and deficiencies. A self-assessments plan is developed and reviewed at the beginning of each year
Management Review Meetings – Review meetings ensure leadership is effectively informed and engaged in driving their respective areas’ performance. These meetings are regularly scheduled to provide management oversight of organizational performance, identify learning opportunities, and support continuous improvement. These should include security stakeholders from throughout the enterprise
Corrective Action Program – CAP is a standard approach for issue resolution that provides a formal list of risk-based prioritized issues, a consistent process to investigate and resolve issues, and a mechanism to track all corrective actions
Peer Groups – Peer groups communicate frequently and meet regularly to collectively analyze/monitor core function performance metrics, identify gaps, and drive continuous improvement and core function oversight and support
This security operating model defines the organization’s agreed-upon approach for responding to security risks and establishes expectations for who is responsible for what. This becomes the baseline against which security performance is monitored.
Organizations too often go directly from strategies, concepts, and objectives to projects, technologies, and procedures, but do not achieve their desired results and struggle to explain why they are doing what they are doing.
The security operating model operationalizes your security strategy—translating broad visions of enterprise security into a set of practical and realistic plans and actions. Security leaders can provide a clear picture of desired security capabilities and corresponding people/process/technology enablers through the operating model.
A security operating model balances risks to the organization within industry expectations and drives decisions about where to invest security resources.
No two operating models are the same, and each organization faces its own unique set of challenges.
Ultimately, security leaders should operate as a conductor in an orchestra, leading multiple instruments in unison around a common piece of music (i.e., the operating model). A deliberate effort must be made to blend their melodies and harmonies to orchestrate the symphony that is successfully securing the enterprise’s mission.
Security professionals seeking to enhance trust with business leaders and demonstrate progress toward a more secure organization with a strategic, rather than reactive, approach to reach security goals should adopt this proven security operating model.
Sussex Economic Advisors is now part of ScottMadden. We invite you to learn more about our expanded firm. Please use the Contact Us form to request additional information.