
Security leaders often struggle to communicate how well they are performing. Similarly, to justify new investments, budget increases, or ongoing costs, security teams find it difficult to articulate the value of security investments. It is not enough to claim we prevented something bad from happening.
Traditional security management and reporting methods often fall short. Heat maps with high/medium/low designations do not have the necessary rigor. Multipage security reports may have the appearance of rigor, but are lacking actual business context. The metrics themselves are often ineffective:
Properly designed security metrics, a core element of the security operating model, help organizations address questions business leaders care about. They want to know if security investments and efforts are achieving their intended results. Metrics must enable the security organization to learn and improve by evaluating security efforts against expectations and adjusting them appropriately.
No two security organizations are the same, and each faces its own set of security issues and challenges. An organization’s metrics should be relatively unique to its situation. Leaders should start with the end in mind, understand what outcomes are necessary (often in the form of risks and risk mitigation), and work backward to develop a metrics package that informs their progress toward these outcomes. An outcomebased approach, similar to the goal/question/metric method, can identify the most critical measures to evaluate the performance of the organization’s security operating model.
This security outcome approach includes the following steps:
The approach is iterative. It must account for both new questions and new outcomes as they arise. And it allows you to truly explore the outcomes and reevaluate outcome confidence as learnings reveal themselves.
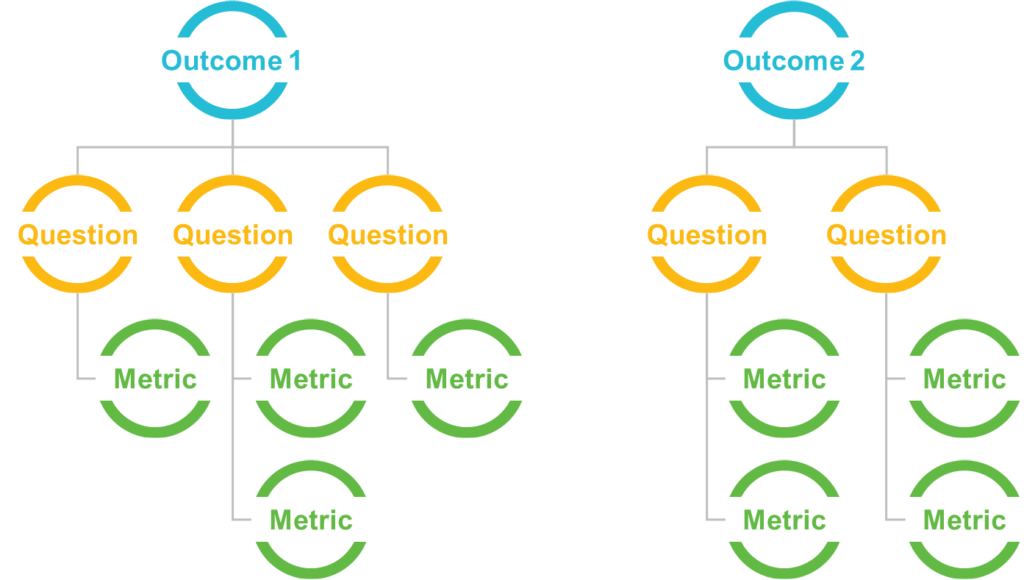
The approach is a powerful way to instrument your security performance—measuring outcomes, not activities. These metrics provide greater visibility and transparency into goal attainment rather than “stick counts.” A secondary benefit is this approach improves goal clarity by forcing outcome definitions to be quantifiable.
For example, a company implements a set of security controls aligned with the NIST cybersecurity framework. In addition to measuring assurance with these controls, each function identifies its top three cybersecurity/physical security risks, pursues risk mitigation, and reports progress. A cybersecurity function identified phishing attacks as a critical risk in need of targeted mitigation. They used the outcomebased approach to develop metrics to monitor their performance:
If developing a security metrics program is a priority for you, connect with a ScottMadden security expert to discuss what you can do to achieve your goals. We would be happy to share ideas as well as additional resources.
View MoreSussex Economic Advisors is now part of ScottMadden. We invite you to learn more about our expanded firm. Please use the Contact Us form to request additional information.