
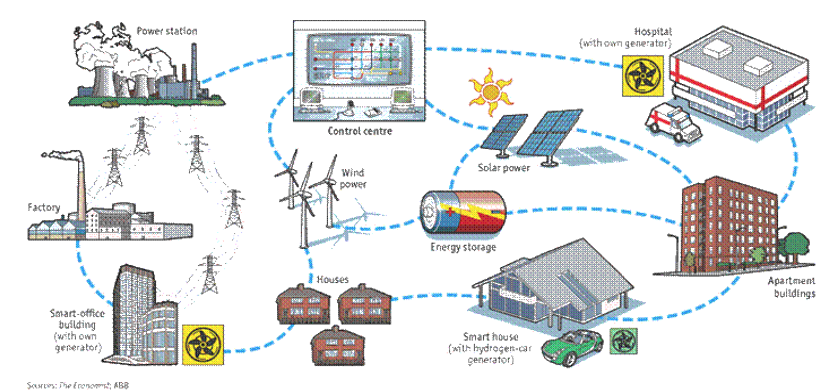
The evolving grid incorporates distributed resources and multi-directional power flows through an abundance of connected assets, increasing the vulnerability of the grid. The utility landscape is adopting communications, sensing, and control systems throughout all levels of the electric grid to make the electric power system more reliable, economical, and environmentally sustainable. EPRI has estimated that the total 20-year investment required for Smart Grid will be between $338 and $476 billion with approximately 70% of those investments for distribution. The increasing number of assets and connections across the grid provides more assets to be secured, vulnerabilities to be mitigated, and risks to be managed. Figure 1 shows a depiction of the chaos (Source: The Economist and ABB).
Figure 1: Electric Grid
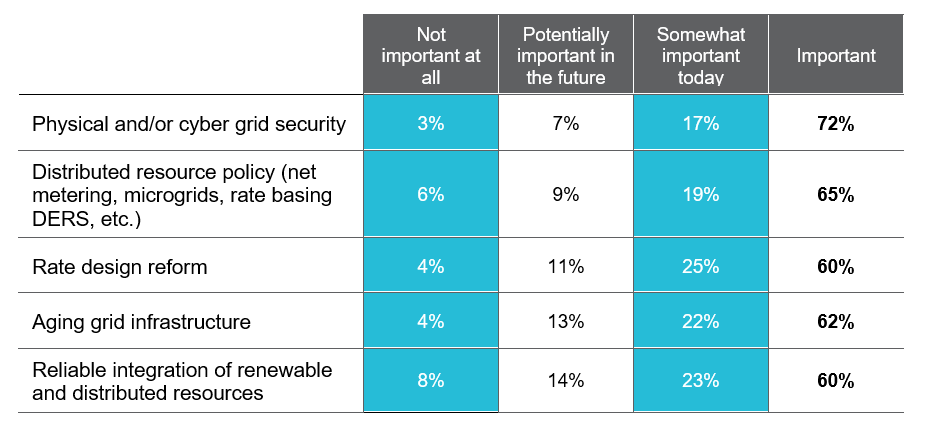
Cybersecurity remains a top concern. Evolving NERC CIP requirements and Federal Trade Commission (FTC) data privacy provisions, as well as a growing number of state-based rules, such as the storage and usage of advanced metering infrastructure data, dictate that data security and information privacy are critical areas of focus. Utility Dive’s most recent State of the Electric Utility Survey named cyber and physical security the most pressing concerns for utilities, with 72% saying it is either “important” or “very important” today. Figure 2 shows the top five power sector issues.
Figure 2: Top Five Power Sector Issues
In many organizations, security efforts are focused almost exclusively on deploying technologies, implementing “best practices,” or responding to a continuous stream of alerts and issues. The result is a reactive security organization, busy with activity and unable to answer the question, “Are we becoming more secure?” The result is friction and distrust between business leaders and the security organization. Security efforts are seen as expensive—doing more to slow the business rather than secure it.
A more strategic approach is necessary. It acknowledges the reality that security needs will always exceed security capacity, provide direction to optimize security resource allocations, and demonstrate progress toward a more secure organization. The security organization’s focus is on identifying risks, recommending responses to these risks, facilitating the appropriate tradeoff decisions related to these risks, and providing line of sight to the execution of these risk responses.
A security operating model enables this approach. It provides governance and oversight of security for the entire organization, where the business is not only a recipient of the security services, but is also instrumental in the collaboration, implementation, and sustainability of security efforts. When viewed holistically, the operating model utilizes a risk-based approach to identify and prioritize risk mitigation efforts to appropriately secure the enterprise’s mission. The core of a security operating model is a collaborative, continuous improvement process designed to sustain the controls that secure the enterprise.
Figure 3: Security Operating Model
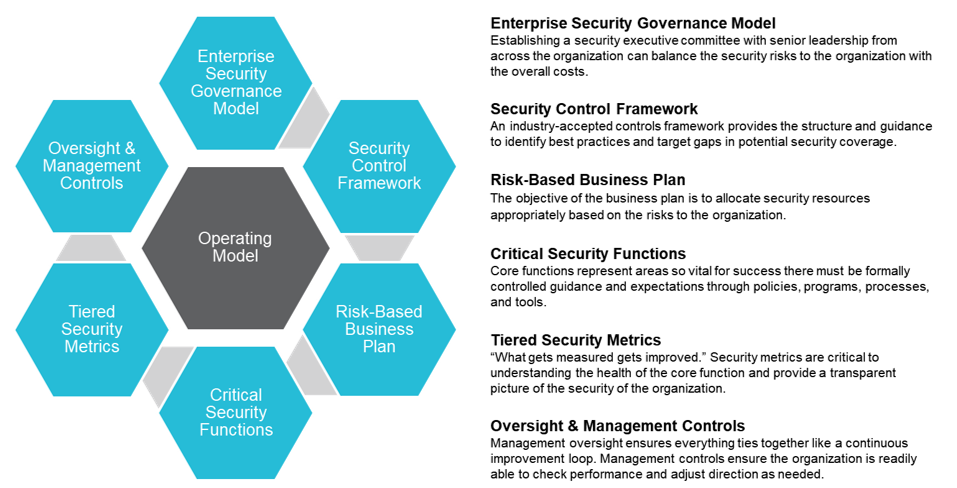
No two operating models are the same, and each organization faces its own unique set of challenges. However, the success of any operating model relies on the following:
For additional information, please view:
Sussex Economic Advisors is now part of ScottMadden. We invite you to learn more about our expanded firm. Please use the Contact Us form to request additional information.