
Public power plays a vital role in how our world is connected today, thanks to a sustained technological evolution. The use of complex systems to manage public power infrastructure and share tremendous amounts of data has improved operations and customer response times. At the same token, there has been a significant increase in cyberattacks that threaten infrastructures, despite the benefits of these technologies: it is becoming increasingly difficult to keep up with the real and growing danger of cyberattacks. System vulnerabilities can expose operations and customers to significant risks. Public power generation community members have a special responsibility and must implement procedures and advanced technology to secure the infrastructure to prevent cyberattacks and mitigate their impact.
Cybersecurity is critical in the age where technology pervades every aspect of modern life. Public power and utilities depend on advanced technology for more efficient operations and service delivery. These innovative technologies can prove vulnerable and require adequate cybersecurity investments to guarantee stable public power and keep the grids safe from malicious actors. Cybersecurity solutions for public utilities provide awareness of system vulnerabilities that could be open to threats and cyberattacks. Adequate investment in cybersecurity ensures customers’ data security and contributes significantly towards a more reliable grid. Cybersecurity is an absolute must to keep public utilities secure.
As the potential for cyberattacks to damage and disrupt energy distribution, coordinated attacks against the energy industry continue to increase: enhancing your cybersecurity programs should be a top strategic priority for your business.
This report, the first in a four-part series focused on strategic priorities for public power, examines the impact of cybersecurity and the building blocks needed to build an effective cybersecurity strategy.

Thanks to an evolving landscape of technology, our world has never been more connected. The use of complex systems to manage our infrastructure and share tremendous amounts of data has improved operations and customer response times. However, despite the benefits of these technologies, it is becoming increasingly difficult to keep up with the real and growing danger of cyber-attacks they bring. Vulnerabilities in your IT and OT systems can expose your operations and customers to significant risks. As a member of the power generation community, you have a special responsibility to secure your infrastructure by implementing controls to prevent cyber-attacks and mitigate their impact.

Concerns over cybersecurity for public power stem from the potentially wide-ranging impacts caused by any disruption to customer service or the grid’s reliability. The resulting cost to a targeted company’s reputation and bottom line from these cyber-attacks can be significant. No executive wants to read the headlines that follow a successful breach, like Target’s admission that hackers compromised 40 million customer records or the unplanned power outage in Ukraine that caused a six-hour outage for almost 225,000 customers. Companies have increasingly felt the impact of cyber-attacks on the bottom line. This year the cost of cybercrime in the utility and energy sectors amounts to $14.8 million – an 18% increase over 2015. Perhaps most alarming for the industry, the energy sector accounted for 35% of cybersecurity incidents reported against critical infrastructure in the last three years, though none so far have caused power outages in the U.S.
As the potential for damaging, coordinated attacks against the energy industry continues to increase, enhancing your cybersecurity programs should be a top strategic priority for your business.
Public power and electric cooperatives represent a significant part of the energy industry, accounting for roughly a third of electricity sales revenues while providing services to more than 80 million people. Despite their large impact on the industry, public power and electric cooperatives have remained insulated from early attempts to provide cybersecurity regulation to the industry. Regulators are beginning to take notice of infrastructure vulnerabilities, and customers and members are growing aware of the serious risks associated with cyber-attacks.
Back in 2009, the federal government enacted standards to help utilities defend themselves from cyber-attacks. The recent updates to the NERC Critical Infrastructure Priorities standards (CIP V5) have expanded the coverage from generation facilities designated by their operators as critical assets to all assets included in the bulk electric system. Energy distributors that operate under 100 kV and local distribution facilities, which include most public power utilities, are exempt from CIP V5 compliance requirements.
After three years of struggling with their implementation efforts, the industry requested an extension to meet the CIP V5 standards. Public power should take note if large utilities and system operators are struggling with compliance. NERC and other regulators may develop future standards to encompass public power assets, and if history is any indication, it is never too early to start your compliance efforts.
In addition to taking note of expanded regulation, public power members are becoming more aware of cybersecurity risks. In a recent consumer cybersecurity survey, 73 percent and 69 percent of respondents identified online purchases and accessing online accounts as activities that generate the most concern. Smart metering devices, demand reduction, energy efficiency initiatives, and online billing all contribute to the digital interaction that your members expect from a utility and are concerned about security. Almost 50 percent of respondents to the survey said they’re taking more precautions compared to last year. While you could view cybersecurity as an internal IT and OT issue, it is a concern for members and employees throughout your organization and deserves a comprehensive perspective.
ScottMadden Consulting has decades of experience helping energy industry leaders navigate business challenges in uncertain regulatory environments. Recently, we have noticed that many energy utilities are struggling to keep pace with policymakers and shifting consumer sentiment about cybersecurity. Our expert consultants found that more than 50% of energy leaders classify the magnitude of cybersecurity threats as high or severe, but only a quarter (26%) agreed that their organization effectively managed cybersecurity risks.
In response to concerns that not all cybersecurity investments are adequate or effective, ScottMadden has developed a methodology to help energy and technology leaders take a more programmatic approach to cybersecurity. We’ve aligned our process with industry standards, including NIST and ES-C2M2, so that you can take a proactive stance toward future regulation. Our methodology will guide you through several steps, including risk identification and a clear roadmap containing objectives, metrics, and change management capabilities.
The first phase of the process focuses on evaluating your enterprise risks and requires that you characterize your most important information assets. Our strategic framework will ensure that managers prioritize their assets based on business impact, not what is easiest to secure. Identifying which information assets support mission-critical business processes end-to-end provides the context for a meaningful risk discussion.
Once you have identified critical assets, you should engage business stakeholders in an enterprise risk discussion–- this makes cyber threats real. Your business community may not have deep knowledge of cyber risks, but the discussion doesn’t need to be overly technical or scientific. Educating business leaders will provide context for the cybersecurity program and create a starting point for a more detailed understanding of specific risks.
Identifying your critical assets and risk areas allows you to start managing cybersecurity as a business process. You can accomplish this by defining your targets and desired capabilities using industry-standard maturity models and then managing those targets as you would any other business process with the help of continuous improvement practices. ScottMadden Consultants have helped clients evaluate their cybersecurity maturity levels, prioritize gaps, and implement improvement programs through a framework depicted below.
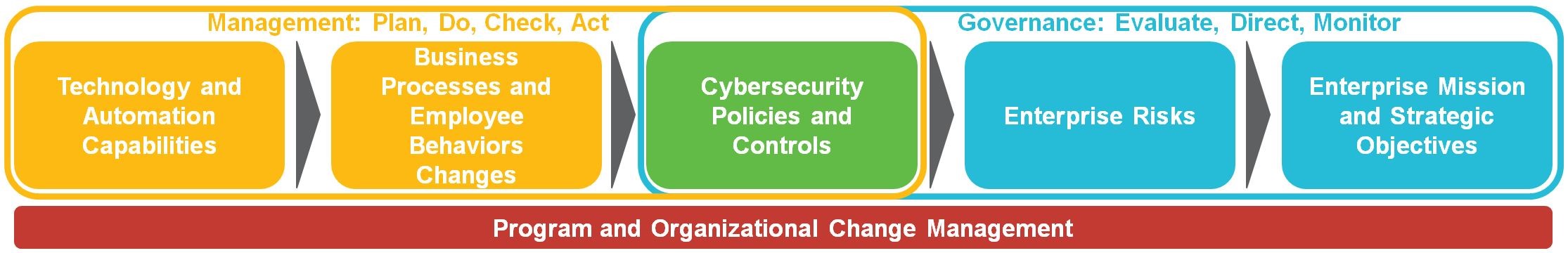
Finally, you can build out your decision-making capabilities and show the value of cybersecurity by developing key metrics. Cybersecurity metrics can reduce uncertainty and build confidence in improvement efforts. We recommend a structured approach to selecting effective metrics, which will answer key questions about your organization’s progress.
This programmatic approach will deliver strategic outcomes by coordinating individual efforts that address the entire system. Often, organizations attempt to build cybersecurity capabilities through a series of individual projects, but this can lead to siloed or disjointed efforts. Our programmatic approach lets you step back and see the big picture while helping you achieve your target security posture.
Public power and electric cooperatives have an opportunity to manage risk through the implementation of cybersecurity programs that address these threats head-on. If you, like other energy leaders, are concerned about upcoming regulations, the growing interconnectedness of your data, or the bottom-line impact of electronic vulnerabilities, please get in touch with us. We can share with you how other utilities have been able to secure their assets and their reputation. ScottMadden has experience-based knowledge that will help you decide what to do to protect your assets, employees, and members and can show you how to do it.
View MoreSussex Economic Advisors is now part of ScottMadden. We invite you to learn more about our expanded firm. Please use the Contact Us form to request additional information.